Hi,
Today I am going to talk about the UAC (User Account Control) give you a brief explanation of what it is and show you the necessary steps to configure UAC correctly.
The UAC allows us to protect our computers preventing users from running harmful software, and discourages users from running any non-relevant installations on their computer.
Using UAC we quite blocking any potential malware initiated on a computer.
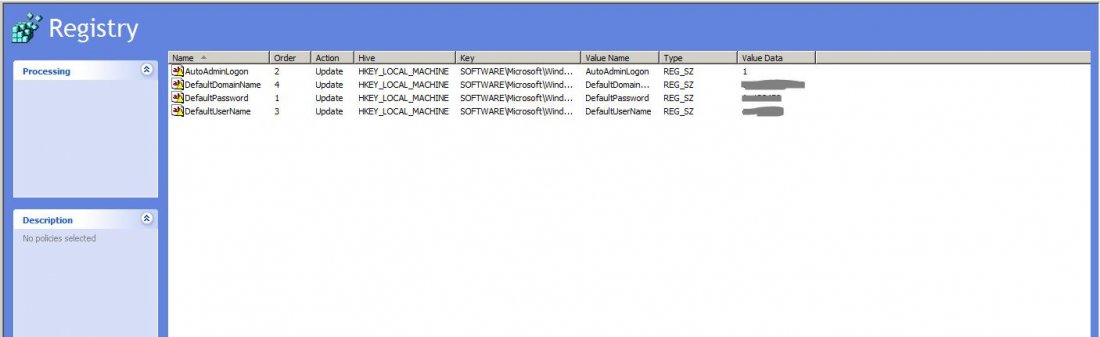
When trying to install /uninstall or even RUN any executable, there are some applications which need to write to locations or registry keys which standard users are not able to. As soon as the executable tries to write in these locations the UAC will appear. if you are a member of Local Admin and the UAC is enabled on the second level [This one is by default in Windows machine] You will not get any notification.
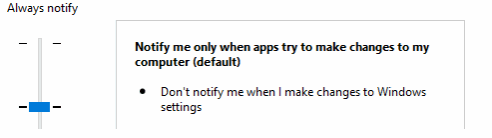
If it is set to the first level, you will always be prompted for any changes even if you are an administrator.
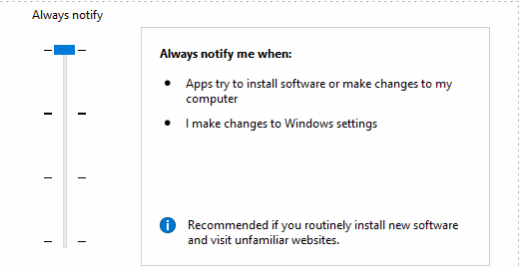
The third level of the UAC will only notify you when an application tries to make changes to system folders or to the registry and will not dim the desktop. The dimming of the desktop is Microsoft’s “Secure Desktop” which will not allow anything to run until the UAC prompt is acknowledged
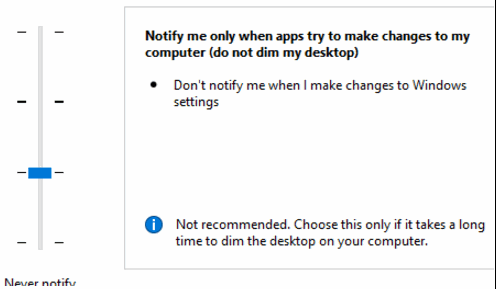
The fourth level will not notify you at all if any applications try to make changes to your computer. This bypasses any security and for that reason, it is not the recommended setting.
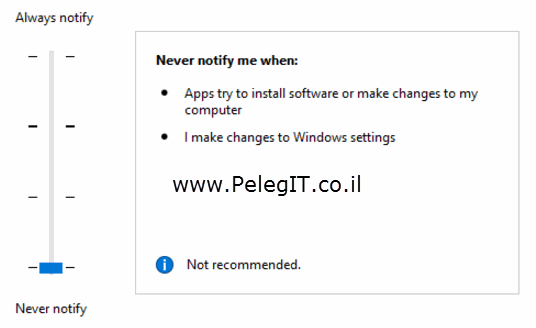
Whichever notch you choose on the slider, as long as you are not an administrator, you will be prompted for administrator credentials to initiate the process.
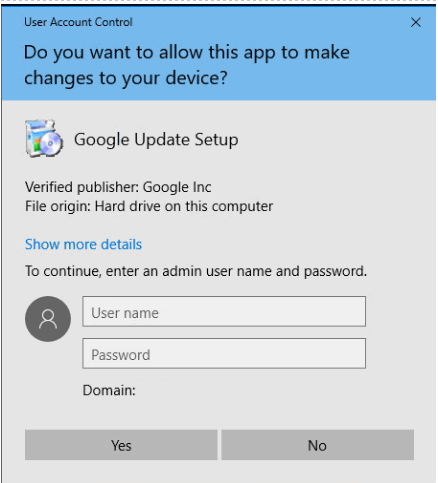
After you install an application and it prompts you to enter your administrative credentials run it, it is because the application was not designed to be UAC Aware. UAC Aware is a development method in which an application will not request elevation using privileges of its parent process. For more information about UAC Aware applications you can check out this site:
https://www.codeproject.com/Articles/17968/Making-Your-Application-UAC-Aware
How can you check your UAC status?
First open CMD and run the following query: [Anyone can run this query]
REG QUERY HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ /v EnableLUA
0x1 means UAC enabled, 0x0 means UAC disabled.
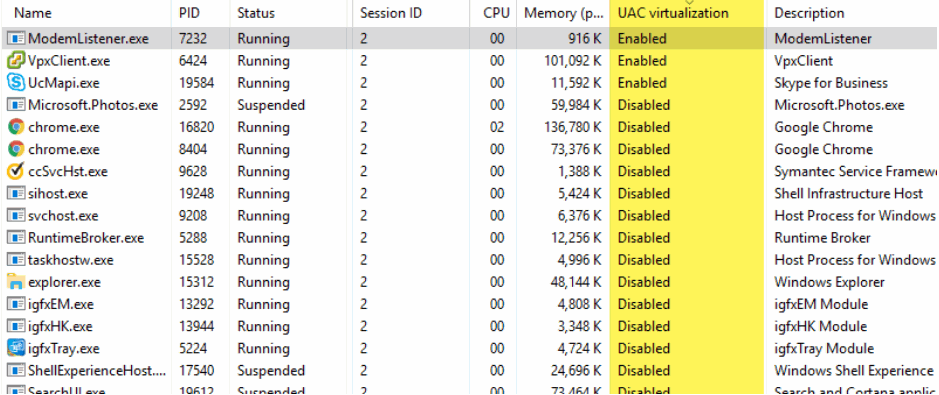
UAC Virtualization helps us prevents applications from writing to protected system locations by redirecting the write actions to a location that user has permission within their profile. To see which applications are using UAC virtualization you will have to add the UAC virtualization column in the Task Manager. Right-click on one of the titles column names and click Select column, check UAC virtualization and click OK
Ok, so let’s talk a little bit about the GPO:
Suggestions configuring the GPO
- No local admins, except Domain Admins & IT-Support. Create a new security group, add any IT members, and then deploy the group by GPO to be Local Admin on your clients.
- To remove any local admin users from your computers, take a look at this article:
https://pelegit.co.il/manage-local-account-users-powershell/
3.Apply the GPO to a security group that contains your computers which are supposed to get this policy. Do not apply this to authenticated user, it is easier to manage the group of computers you want the GPO applied to than adding exceptions to the ones you don’t want it applied.
Policy to configure:
Computer Configuration > Policies > Windows Settings > Security Setting > Local Policies/Security Options >User Account > Control > Policy Setting
User Account Control: Admin Approval Mode for the Built-in Administrator account Enabled
User Account Control: Allow UIAccess applications to prompt for elevation without using the secure desktop Enabled
User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode Prompt for consent
User Account Control: Behavior of the elevation prompt for standard users Prompt for credentials
User Account Control: Detect application installations and prompt for elevation Enabled
User Account Control: Only elevate executables that are signed and validated Disabled
User Account Control: Only elevate UIAccess applications that are installed in secure locations Disabled
User Account Control: Run all administrators in Admin Approval Mode Enabled
User Account Control: Switch to the secure desktop when prompting for elevation Disabled
User Account Control: Virtualize file and registry write failures to per-user locations Enabled
If there is a department in your organization which should not have the UAC elevations (e.g Research and Deployment), make sure they are local administrators of their computer and then you can apply a GPO which will only be applied to their computers. Make sure when you create the GPO you apply it to the security group of the computers and do not apply it to authenticated users.
User Account Control: Admin Approval Mode for the Built-in Administrator account Disabled
User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode Elevate without prompting
User Account Control: Behavior of the elevation prompt for standard users Prompt for credentials
User Account Control: Detect application installations and prompt for elevation Disabled
User Account Control: Only elevate executables that are signed and validated Disabled
User Account Control: Only elevate UIAccess applications that are installed in secure locations Disabled
User Account Control: Run all administrators in Admin Approval Mode Disabled
User Account Control: Switch to the secure desktop when prompting for elevation Disabled
- Another suggestion from my point of view, is, if you are Sys Admin, work with two account, one for routine work (Login to computers) second for Administrations (Servers, Configurations and so on, Yeah, I know, it frustration to work with two accounts, but trust me once you get ransomware it will be more frustration)