Hey guys, if you recall, a few months ago I posted a great new article about a new security possibility called Exploit Guard -In that article, I did my best to summarize everything related to configuring and applying this security possibility using Group Policy. If you want to read more about this, please follow this link:
https://www.pelegit.co.il/windows-10-new-security-features-eg/
So, today I’d like to go over how to deploy this security possibility to accomplish the same purpose using SCCM.
We already know a little bit about Exploit Guard requirements:
Attack Surface Reduction Devices must have Windows Defender AV real-time protection enabled.
Controlled folder access Devices must have Windows Defender AV real-time protection enabled.
Exploit protection –
Network protection Devices must have Windows Defender AV real-time protection enabled.
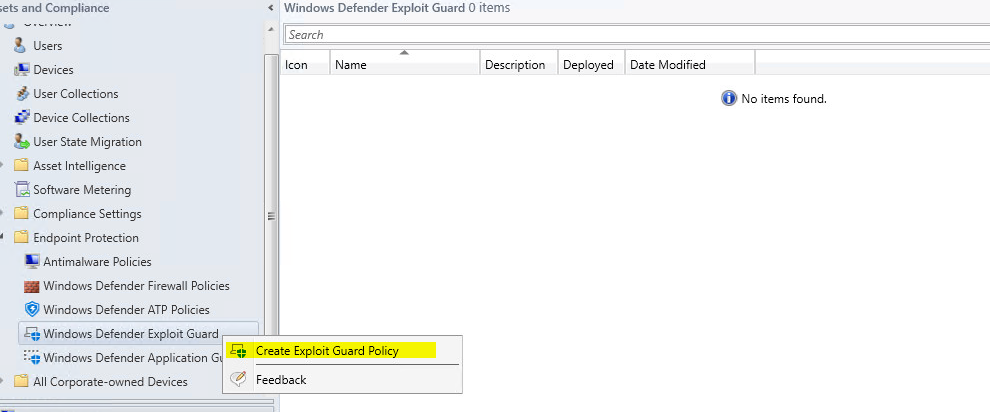
When updating the System Center to 1802, you can see that they offer the “Windows Defender Exploit Guard” as an available feature. Once you enable it and install the update you will see under “Assets and Compliance” > “End Point Protection” the “Windows Defender Exploit Guard” available:
Let’s see how to deploy this:
Now we have to state some general information for EG. I’m going to leave off on “Exploit Protection” for a moment.
EG requires an XML file which is not available to me right now.
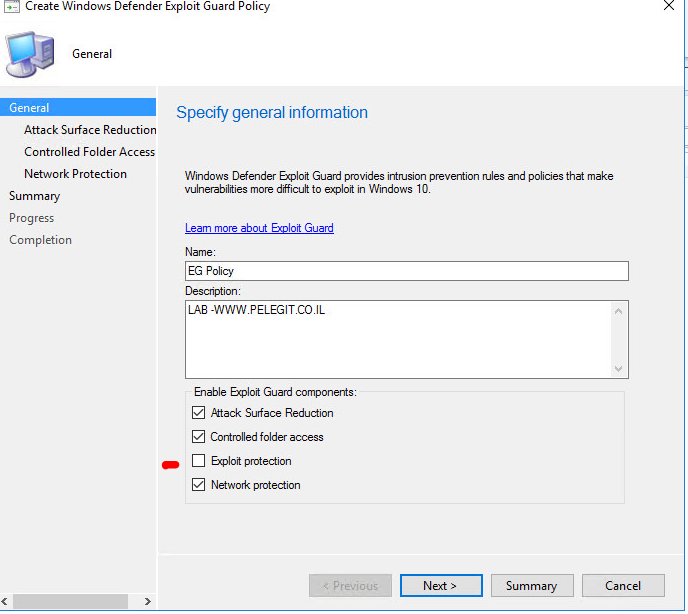
The first step is to configure the “Attach Surface Reduction” with the following options:
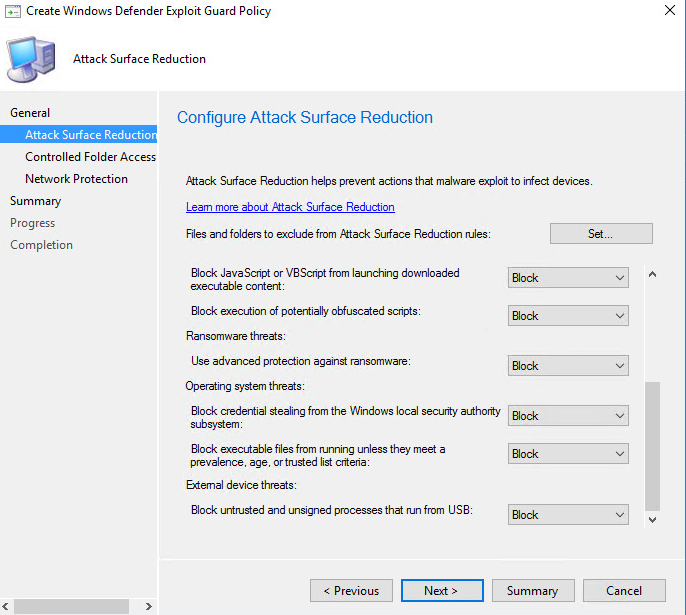
Controlled Configure the Folder Access which blocks malicious or suspicious apps.
You should also insert apps which are allowed to make changes in the protected folders.- For example:
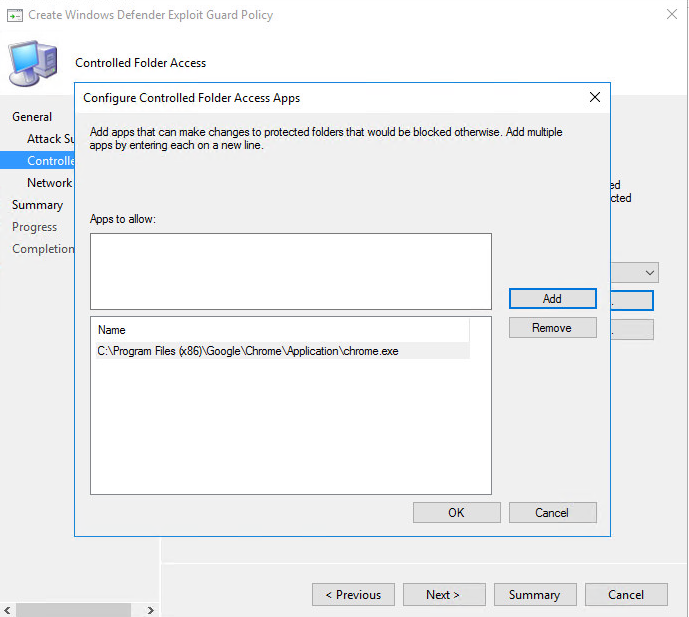
Set protected additional folders:
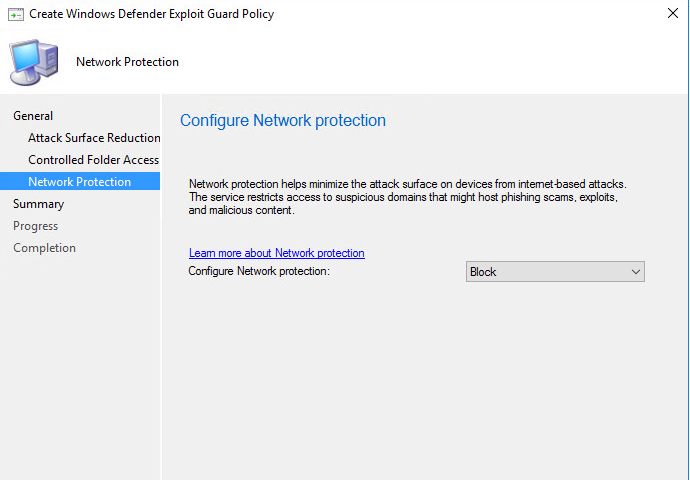
Configure Network protection:
And most important- Deploy the policy to the certain collection:
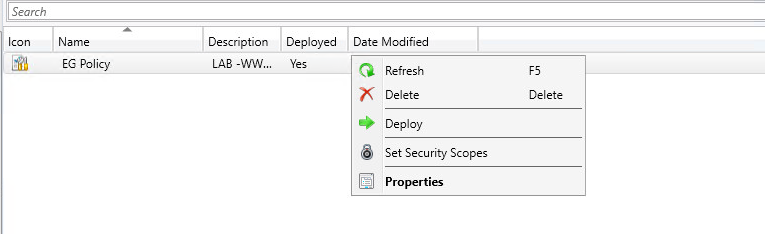
After 30-40 minutes the clients get the policy:
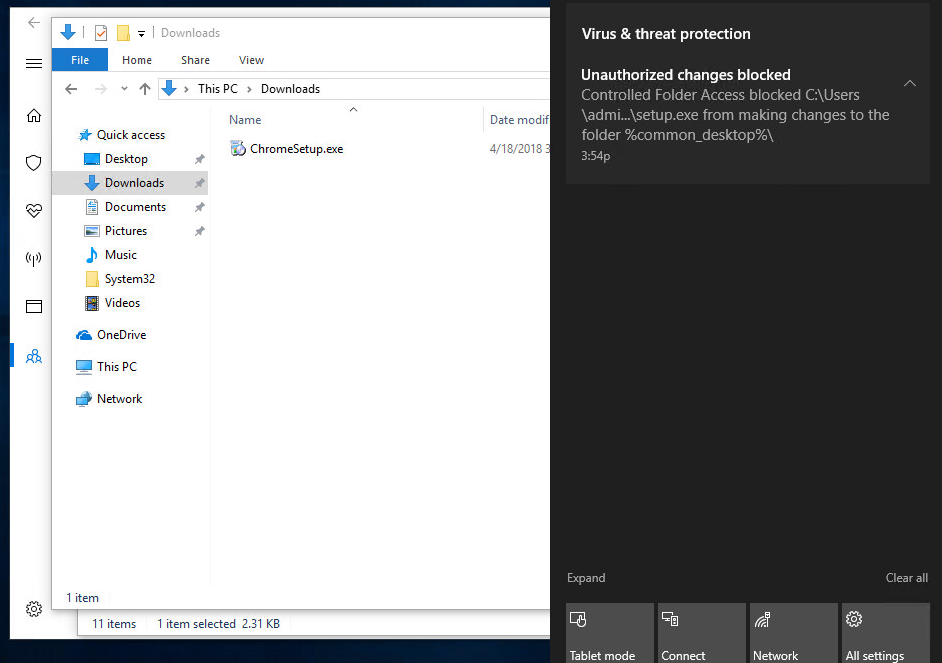
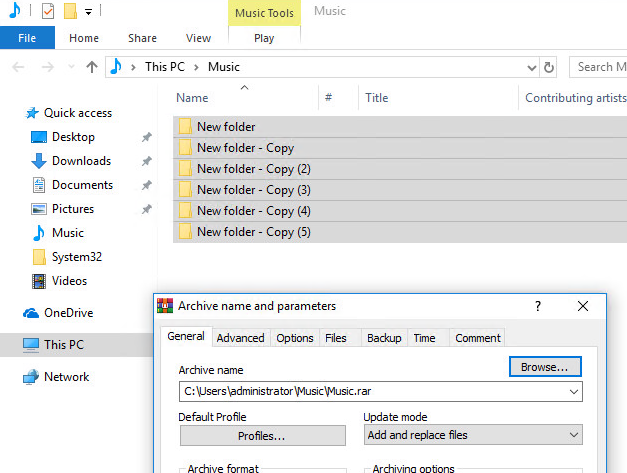
Try to compress several folders with “Winrar” and save into protected location:
Getting an error? Asking yourself why? It’s because the Music folder is a protected folder by default, by reason of its user personal folders, Winrar is not going to allow it to make any changes to protected folders.
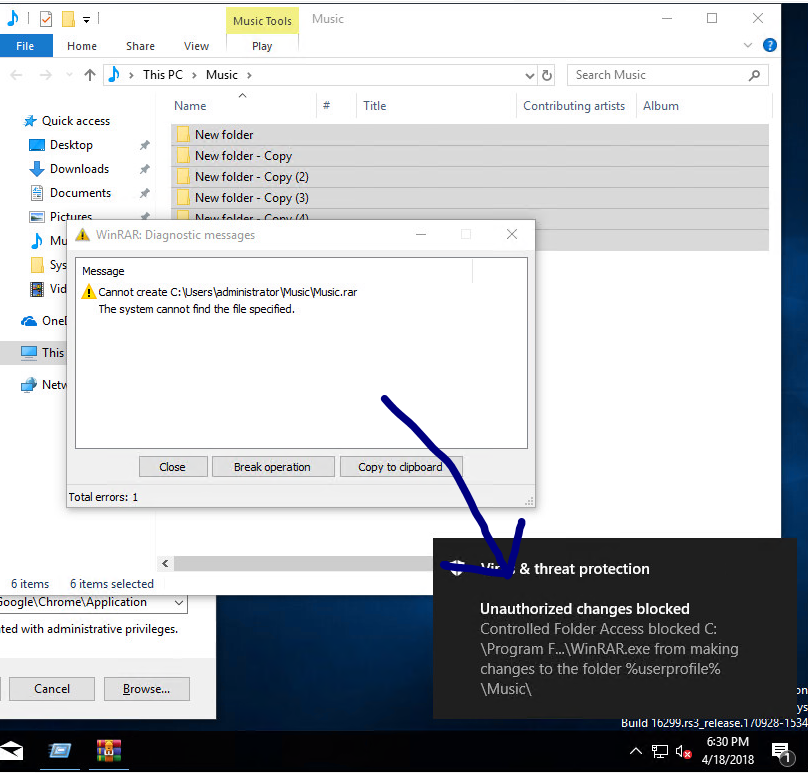
So let’s allow the Winrar in our Controlled folder access (from the client side, you can do the same on SCCM)- and now it works
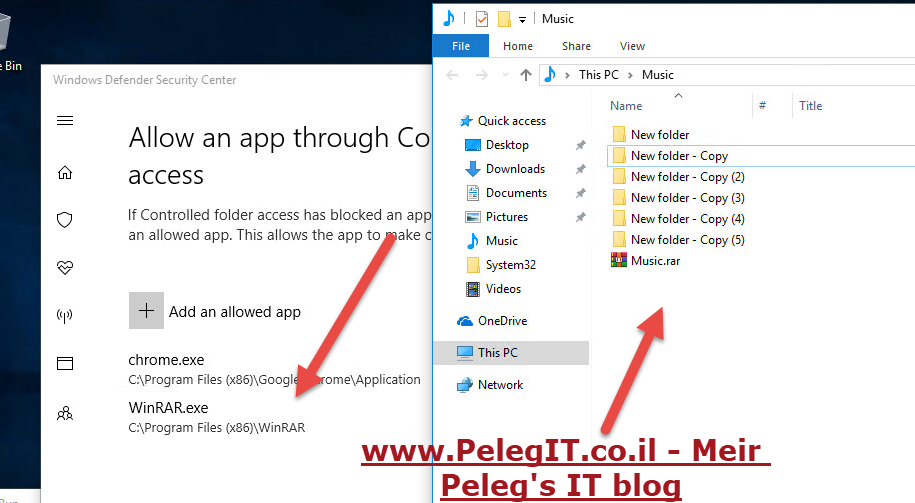
FOA, In conclusion, if you are using CFA and you aren’t allowing a certain app to run on the protected folder you won’t be able to do any action with that app on the protected folder – You must allow the App!
Secondly, you can add some folder’s paths which can be protected location as well, by default windows folder and user folder are protected, but sometimes there are some location which should be added manually if you want them to be protected.
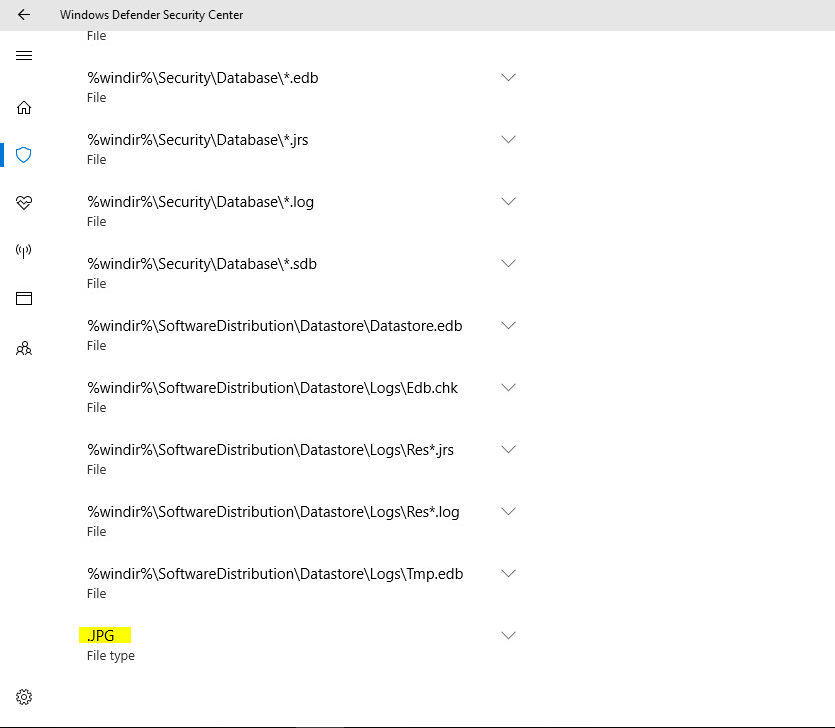
My endpoint antimalware policy set to exclude JPG:
This type of excluding just helps the scan complete faster… these paths will be skipped
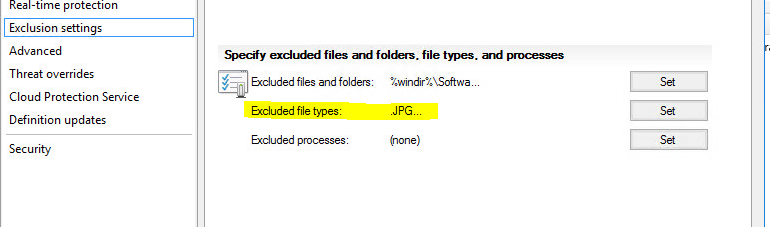
File excluded from a client: