Hey guys,
It is quite well known and not a secret that Microsoft wants being involved and be a major player in anti-virus worlds, they are increasingly pushing the endpoint protection as security solution to many customers, and to be sincere the Endpoint protection does a perfect job!
In this article, you are going to see how to enable and deploy the SCEP (System Center Endpoint Protection) and afterward, I will show you how to create the necessary antimalware policy and custom client device settings and at the end, we will deploy them together.
System Center Endpoint Protection allows us to manage our end clients security using install the endpoint agent, the entire management is using SCCM and we are getting basic management of Real-time, windows firewall, scan process, malware and Spyware detection, remediation, Critical vulnerability assessment, Network vulnerability detection and more option that you going to reveal.
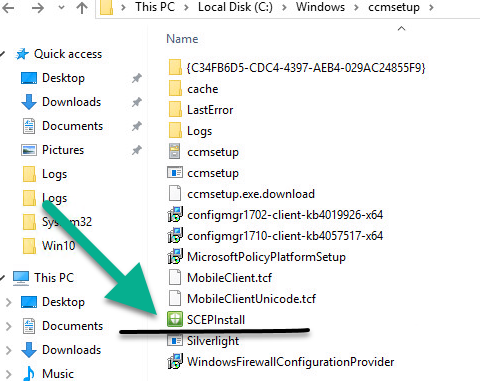
SCCM deploys the endpoint under “scepinstall.exe.”, therefore, you must allow this file from running, the installation exists on the site server and not on the client side:
C:\Windows\CCMSetup\
You can deploy the agent manually and even assign the antimalware policy using the following command:
scepinstall.exe /policy <full path>\<policy file>
In a case you want to capture a new image with “scepinstall.exe” you must delete some important registry key– follow the steps:
- Download the Psexec.exe.
- Run the following run.
Psexec.exe -s -i regedit.exeit will open the Registry Editor with LocalSystem privileges. - And delete the registry keys: – DON’T restart the computer again! if you do, you must remove the keys again. (they are created while endpoint protection client starting)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft Antimalware\InstallTimeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft Antimalware\Scan\LastScanRunHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft Antimalware\Scan\LastScanTypeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft Antimalware\Scan\LastQuickScanIDHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft Antimalware\Scan\LastFullScanIDHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RemovalTools\MRT\GUID - Create quick capture using DISK:
- https://www.youtube.com/watch?v=qFkz6g3rA-0
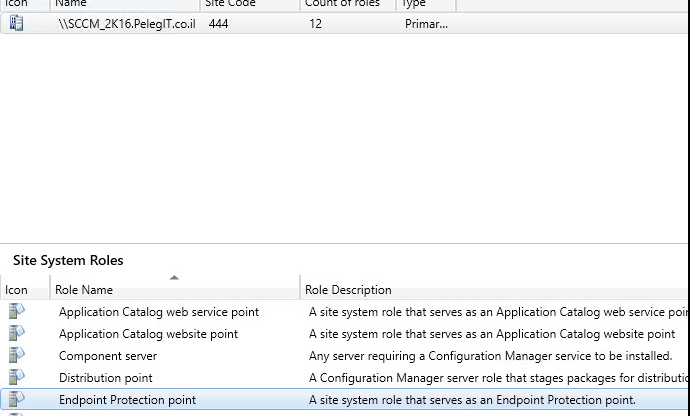
Before we start we should add the “Endpoint Protection Point” Role to our DP:
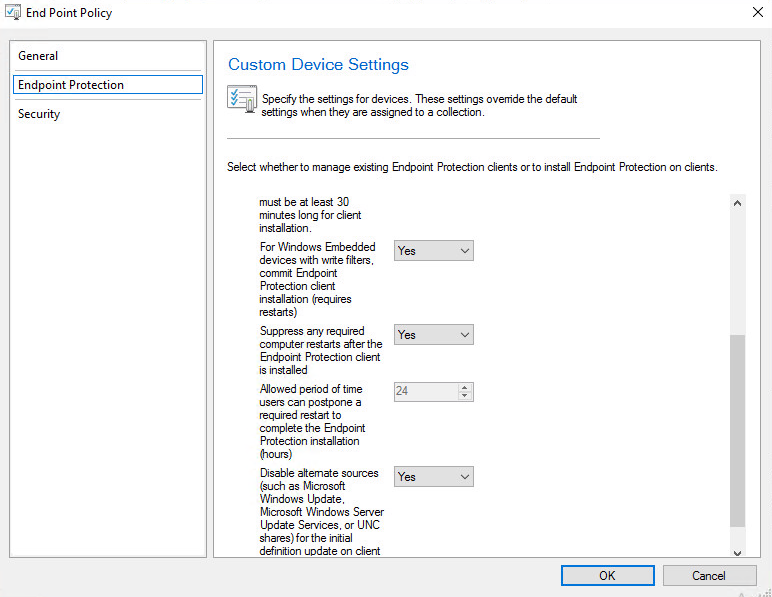
Navigate to “Administration > Click Settings > and create new “Custom Client Device Settings”
If your custom device settings are marked as grayed-out, it means that you haven’t installed the “Endpoint Protection Point Role” yet.
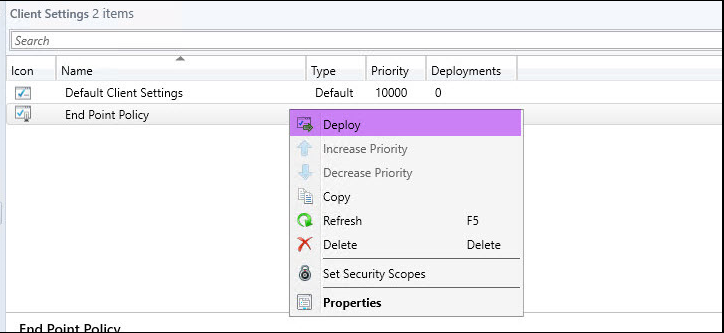
Then, we should deploy the Endpoint Custom Policy to the certain collection:
Select the collection you would like to deploy
You should wait about 20-30 minutes upon you see the endpoint activity on the Endpoint Protection States:
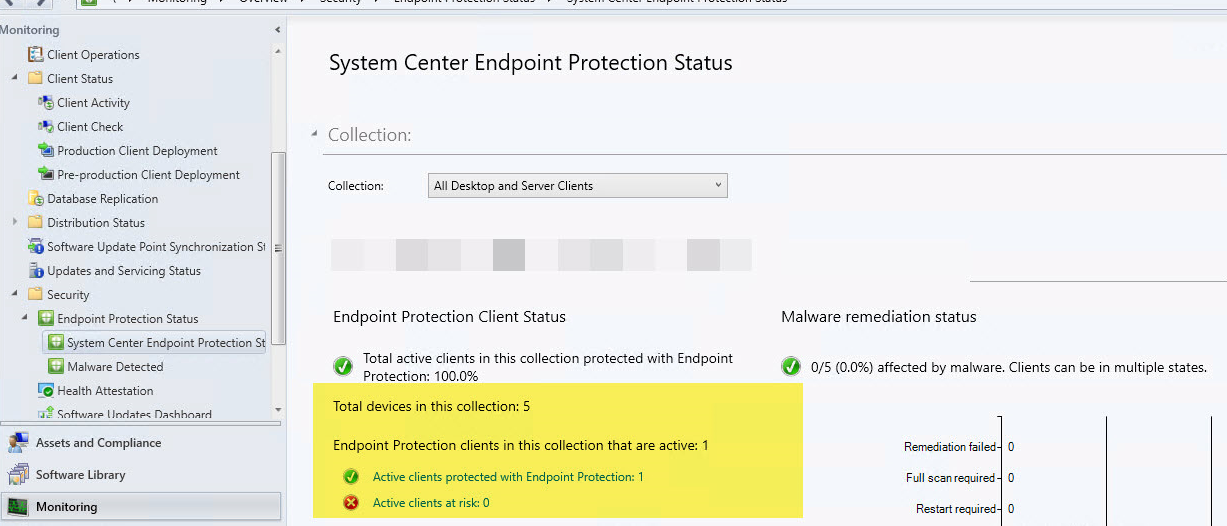
Clients will be configured with these settings in the next download client policy cycle unless you will apply then manually using SCCM extensions.
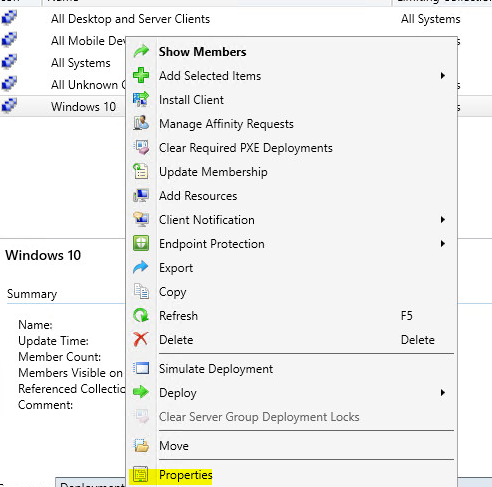
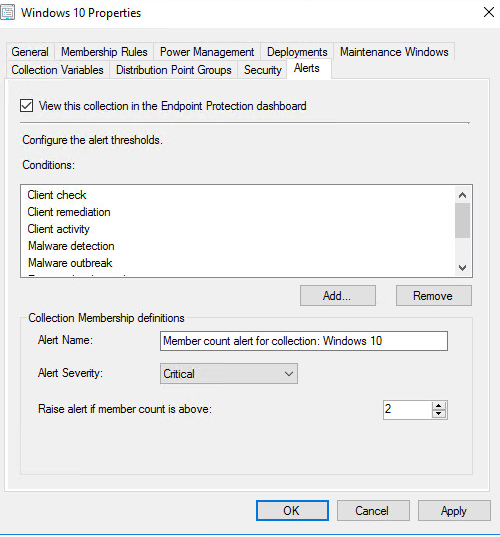
We should add our collection to alert, right click on your collection and then click on properties:
And make the “View this collection in the Endpoint Protection Dashboard”:
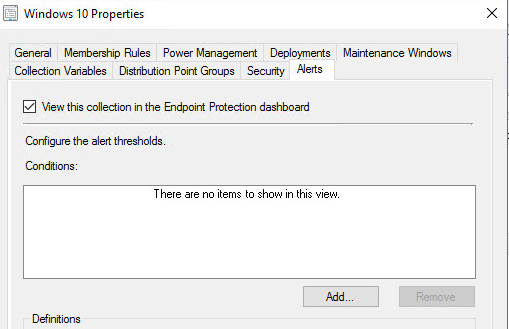
Click on “Add” button and allow the following checkboxes:
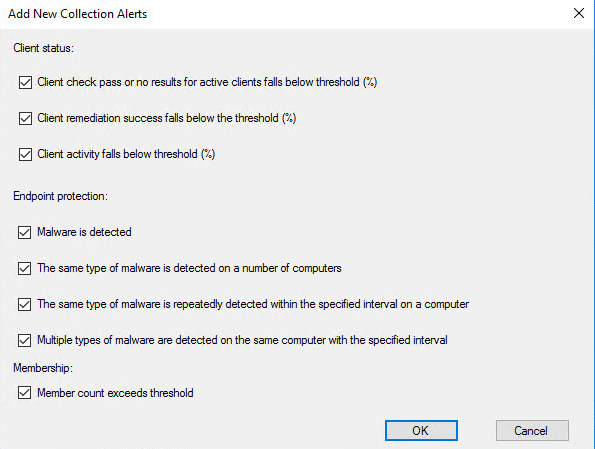
Settings:
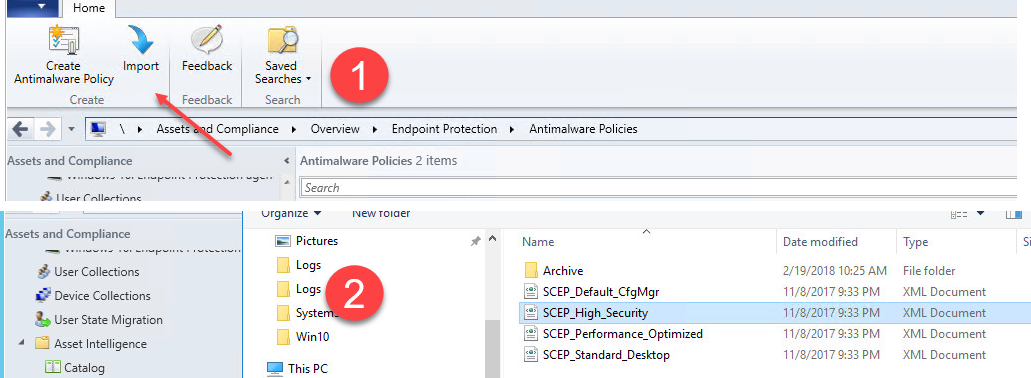
Post Endpoint deployments, we should create a new antimalware policy, or use on some available default EndPoint Protection antimalware policies which can be imported and suits to our policy settings, if you want to use them you can click on “Import” and then select one of them:
However, I would like to create my own Antimalware policy:
Go to “Assets and Compliance” and the to “EndPoint Protection” > Right click on Antimalware Policies “Create Antimalware Policy“:
And choose the relevant policies settings.
Enable real-time protection Set to Yes to configure real-time protection settings for client computers.
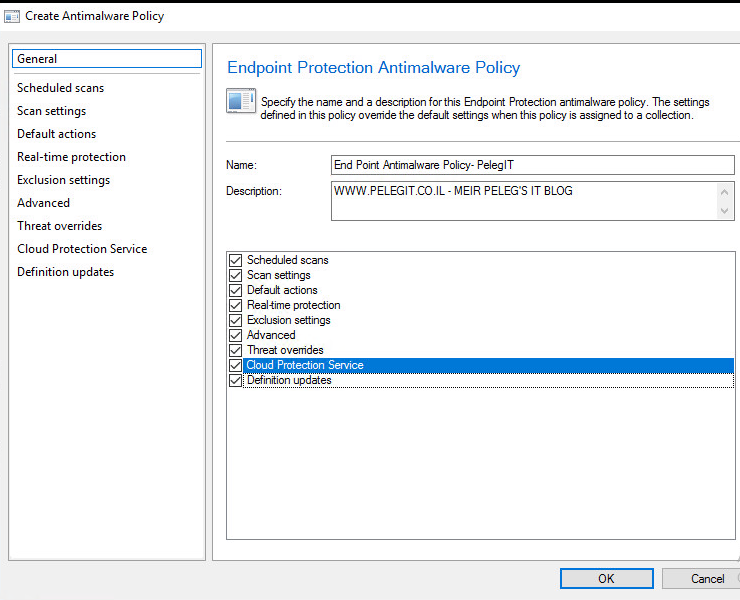
By going over the policy you can enable the settings you would like –
Exclusion Settings:
Process excluded, files, folders-
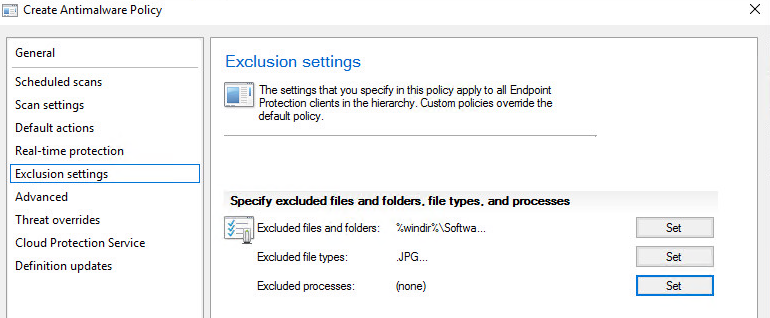
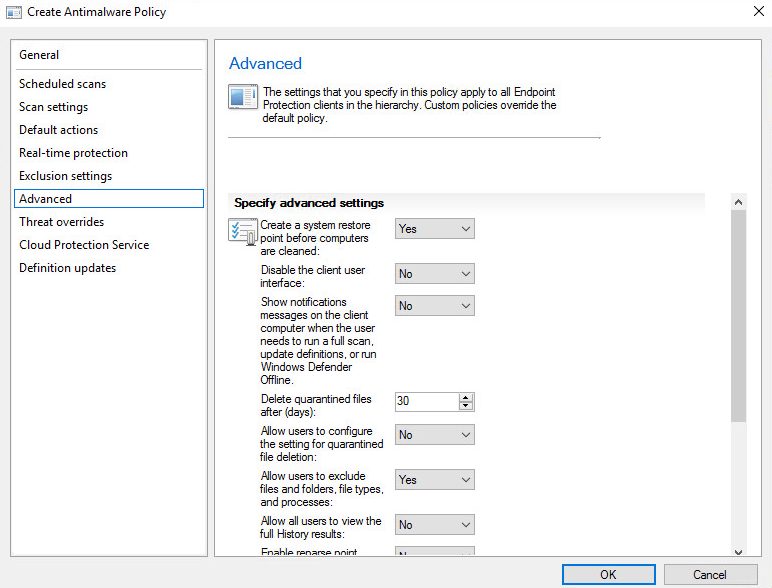
Some important settings on “Advanced“:
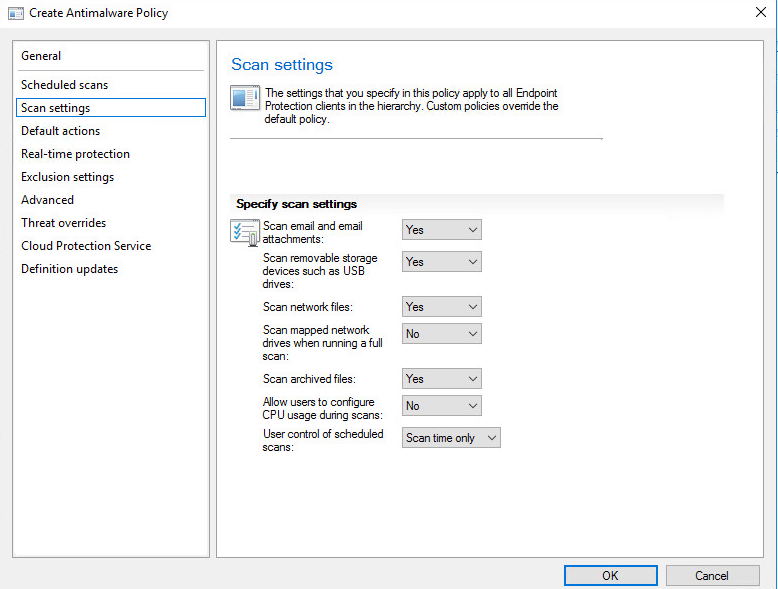
Scan settings:
As you see, there are many policies which definitely can make an internal noise, I strongly recommend you to go over the following TechNet List of Antimalware Policy Settings website and set it up accordingly to your requirements:
- Scheduled Scans Settings
- Scan Settings
- Default Actions Settings
- Real-time Protection Settings
- Exclusion Settings
- Advanced Settings
- Threat Overrides Settings
- Cloud Protection Service
- Definition Updates Settings
Once you’ve completed the configuration click on OK, then right-click and “Deploy“- select the collection you want:
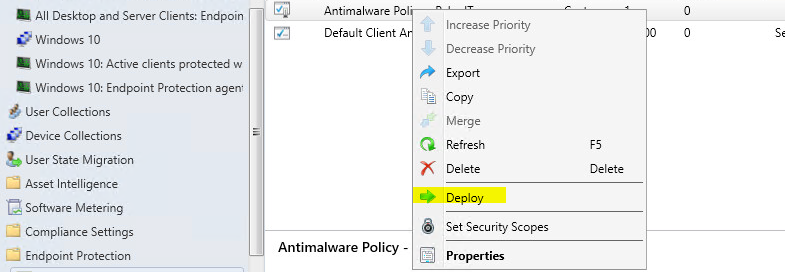
In a case you are using ADR (Automatic Deployment Rule) for deploying windows updates, you should enable the (latest definitions updates) “Forefront Endpoint Protection 2010” on your products:
If you are syncing windows update against your WSUS server you should enable this over there as well.
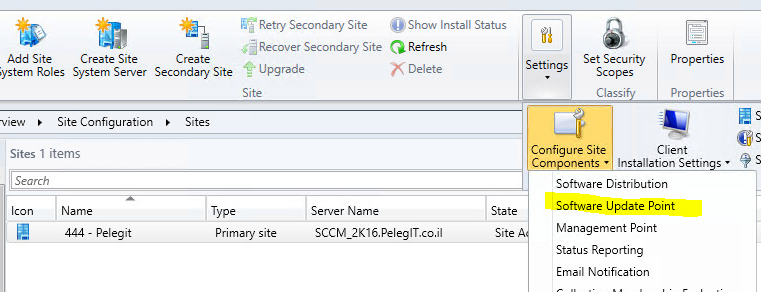
Checkbox the “Forefront Endpoint Protection 2010″:
Then you have to run the”Synchronize Software Updates”.
If you are experiencing any issue with EndPoint Protection Role, I would suggest you go over the following Logs files:
EndpointProtectionAgent.log – Client:
Records details about the installation of the Endpoint Protection client and the application of an antimalware policy to that client.
EPCtrlMgr.log- Site system server
Records details about the synchronization of malware threat information from the Endpoint Protection role server into the Configuration Manager database.
EPMgr.log – Site system server
Monitors the status of the Endpoint Protection site system role.
EPSetup.log -Site system server
Provides information about the installation of the Endpoint Protection site system role.
You can verify your policy on the following registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\CCM\EPAgent\LastAppliedPolicy
Or run the following query:
reg query HKLM\SOFTWARE\Microsoft\CCM\EPAgent\LastAppliedPolicy /f 2 /d
And another comfortable way is by clicking on “About” in the Windows Defender:
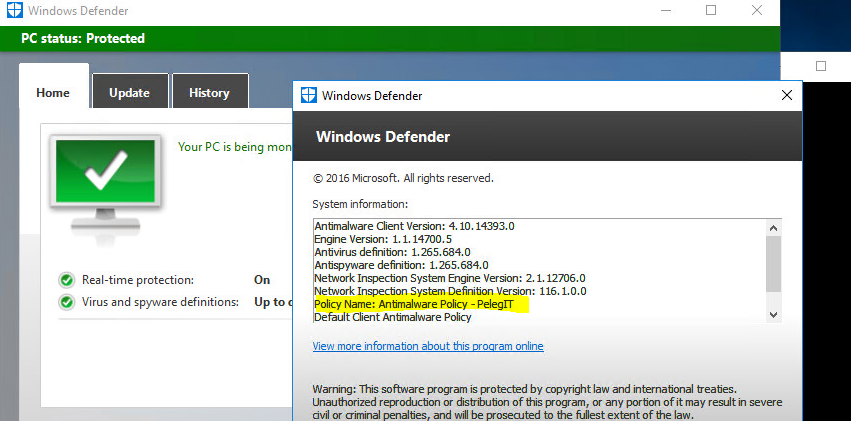
Import note:
https://social.technet.microsoft.com/Forums/en-US/f749efc1-793b-414e-9974-d0728165efed/system-center-endpoint-protection-wont-install-on-windows-10?forum=FCSNext
If you manage endpoint protection for Windows 10 computers, then you must configure System Center 2012 Configuration Manager to update and distribute malware definitions for Windows Defender. Because Windows Defender is included in Windows 10, an endpoint protection agent does not need to be deployed to client computers.